
WE ALL KNOW SOMETHING DOESN’T ADD UP…
If you’re like most Americans, you have this gut feeling that our election system is broken.
You want to know for sure if there was fraud in the 2020 and 2022 elections. Most of all, you want the confidence that your vote will be fairly counted in 2024!
You deserve answers, and you have the right to see all the evidence for yourself. But here’s the problem: those complicit in election fraud will shut down anyone with the audacity to challenge them. That’s an injustice to every American citizen, including you.
The powerful and the privileged do not want the “common man” asking questions. As our Founding Fathers knew all too well, “with the corruptions of time and party,” government will slide toward “the despotism of an oligarchy,” as Thomas Jefferson wrote.
Even though America was founded on the idea that, as James Madison put it, “the People are the only legitimate source of power,” that power has been stolen. Those who would abuse our system see everyday Americans as beneath them; we have only the right to remain silent and obey. They have forgotten that they work for “We the People.”
Mike Lindell hasn’t forgotten.
Mike believes that Democracy and Freedom will die if we cannot exercise our First Amendment Right to challenge those in whom we’ve entrusted our Natural Rights. That’s why he’s been tirelessly pursuing the truth for years, spending millions of hard-earned dollars, weathering attacks by the media, public ridicule and corrupt lawfare.
And—you know what? MIKE WAS RIGHT! The evidence of fraud is clear and overwhelming. That’s why Mike is exercising the People’s fundamental right to petition the U.S. Supreme Court for the redress of grievances that affect us all.
Noah was ridiculed... until it started to rain.
Mike Lindell has been derided by the media and late night hosts as a conspiracy theorist. He has been sued by voting system manufacturers for defamation when he exposed the security vulnerabilities of our voting systems. His detractors have gone after his business and his employees in order to silence him. In short, those complicit with the theft of our elections and our voice at the ballot box are aggressively seeking to shut down Mike’s voice. Despite all of these attacks, Mike has stood firm and relentlessly promoted the truth about our elections with the support of donors to the Lindell Offense Fund. The faith that these donors have put in Mike’s message regarding our election systems has not been for naught. Today, we have more compelling evidence than ever that…
56%
Believe cheating is likely to affect this year’s election.
16%
Believe cheating is not likely at all to affect the election.
Source: “Election Integrity: 54% Say Not Enough Done to Prevent Cheating.” Rasmussen Feb. 23, 2024
If you don’t want to go into the 2024 elections with lingering doubt, tell everyone you know,
“Mike Was Right!”
What Mike Said...
- "VOTING MACHINES CONNECTED TO INTERNET"
- "MACHINES ARE NOT SECURE"
- "ELECTION SYSTEMS WERE MODIFIED BY FOREIGN NATIONALS"
- "CAST VOTE RECORDS REVEAL THE ELECTION THEFT PLAY-BY-PLAY"
- PCAPS SHOW CYBERATTACKS SHIFTING VOTES"
What His Detractors Said...
- "voting systems are by design meant to be used as closed systems that are not networked meaning that they are not connected to the internet"
- "Most secure election in American history"
- "We have no indications that any foreign actor attempted to alter any technical aspect of the voting process in the 2020 US elections, including voter registration, casting ballots, vote tabulation, or reporting results"
- Cast Vote Records don't exist
- "Hammer-and-Scorecard theory...was nonsense and a hoax"
What the Evidence Says
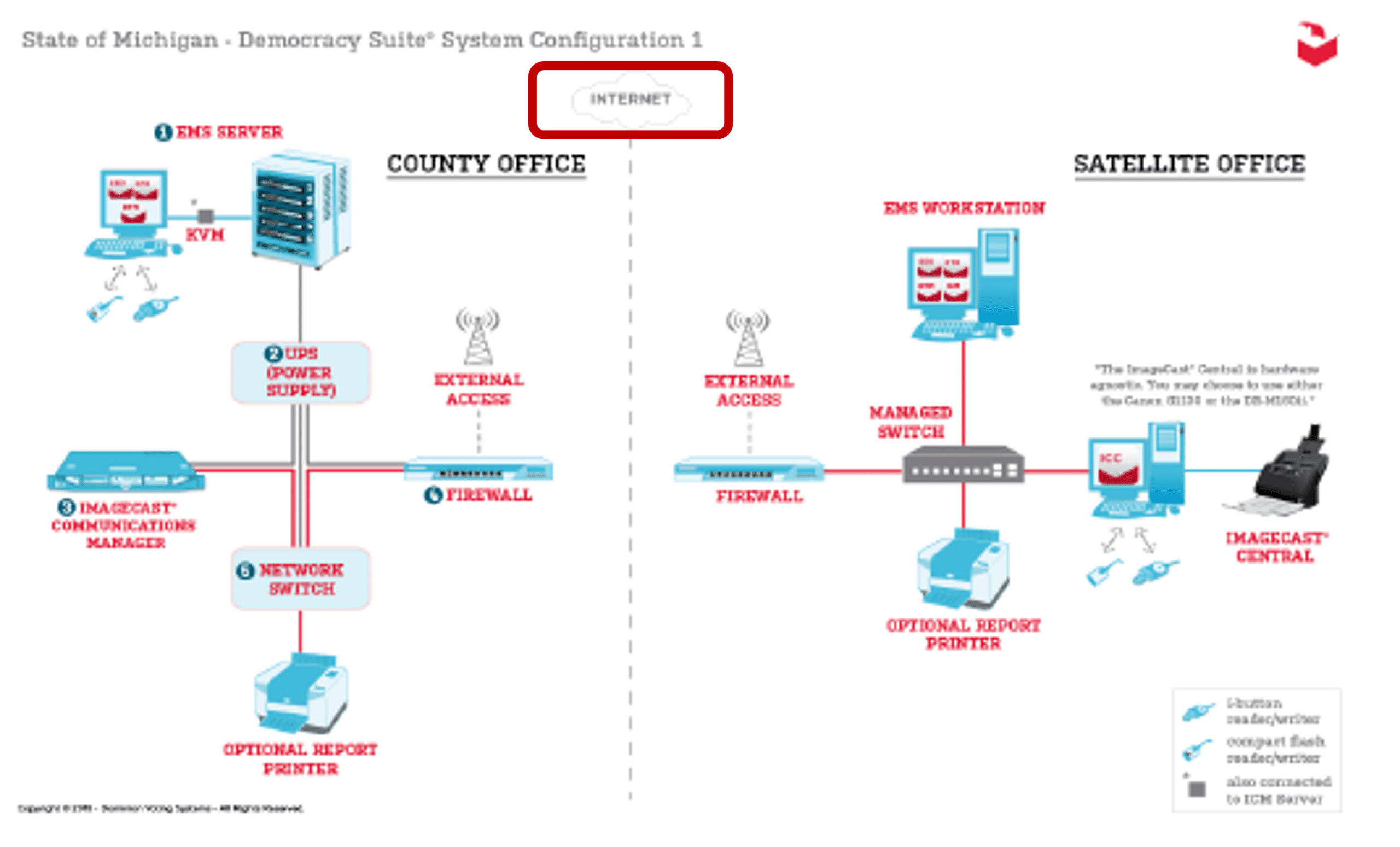
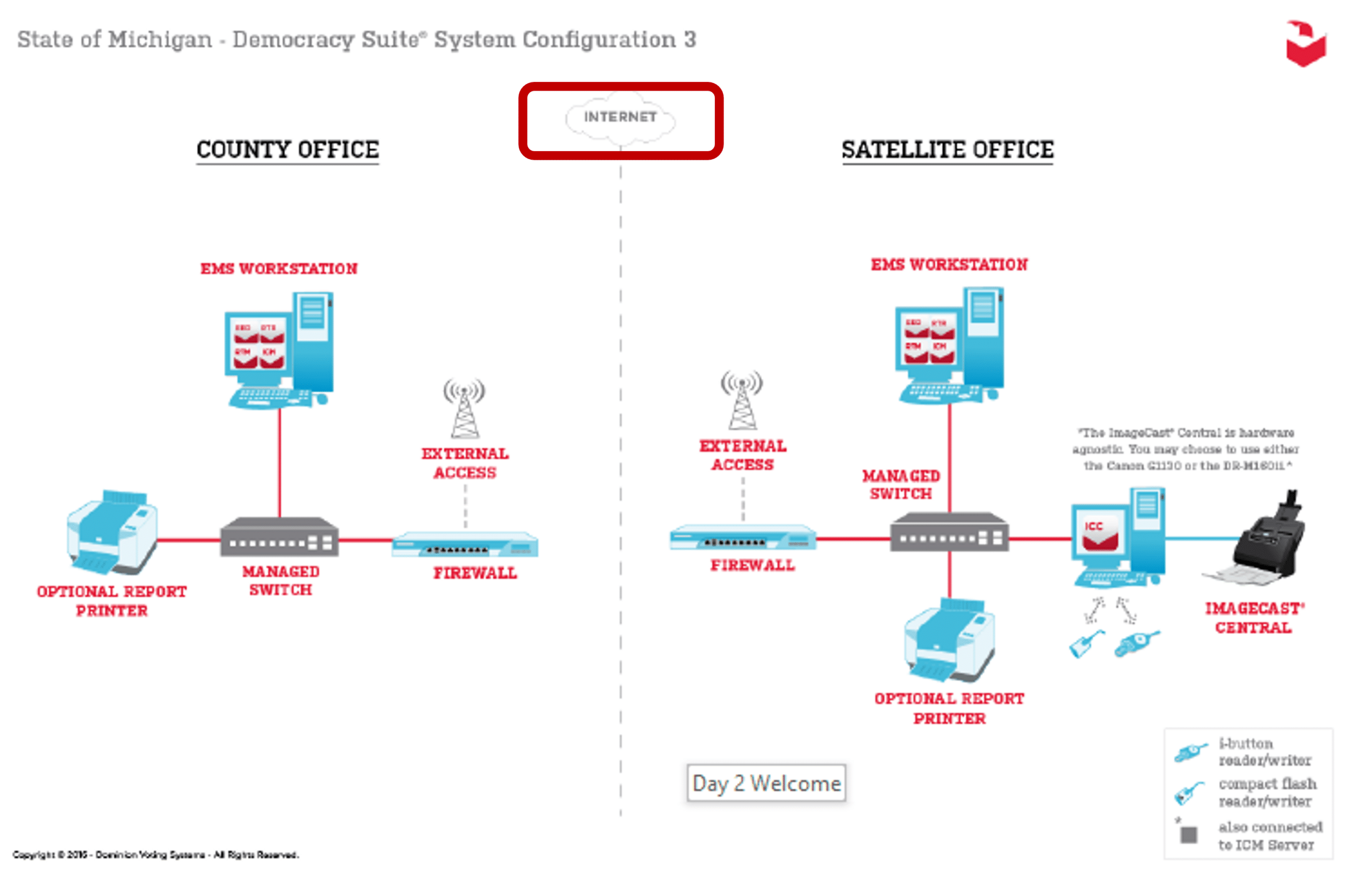
SUMMARY: Electronic voting systems are designed to be connected to the Internet and they were indeed connected to the Internet during the election.
WATCH: South Carolina Voters Unable to Vote Without Internet
** Due to a protective order, the Lindell Offense Fund has removed all references to support this claim that was posted on X.com by @SheriffLeaf. **
• Government contracts with Dominion reveal that their electronic voting systems are designed to connect with the internet.



• Dominion documents indicate their usage of modems which enable internet communications.
** Due to a protective order, the Lindell Offense Fund has removed all references to support this claim that was posted on X.com by @SheriffLeaf. **

• Dominion government proposal features pricing for wireless modems.

• Dominion’s electronic voting systems are not only designed to connect to the internet, they were connected to the internet during the election per exhibits in Bailey v Antrim County.



• Evidence of electronic voting systems being connected to the internet was also found in Maricopa County, AZ, Mesa County, CO, and elsewhere in Michigan.
In Maricopa County, AZ, the audits by county officials failed to reveal any internet connections, yet a considerable number of internet connections were discovered in unallocated space on the county Election Management System (EMS) servers.

This indicates that someone had attempted to erase evidence of internet history but failed to reformat the server hard drive containing such data. The internet history that was recovered from unallocated space indicates that the server attempted to connect to the internet upon startup.

Furthermore, there is evidence of multiple visits to external IP addresses.

Internet connectivity is not limited to Dominion systems: Bailey v Antrim County investigations revealed the existence of a 4G Wireless Modem installed on the motherboard of an ES&S DS200 voting system.

Furthermore, there was log file evidence that this system had been connected to the Internet.

In case this is not enough evidence in support of the assertion that electronic voting systems are designed to be connected to the Internet, note that the Federal Government contracts with an organization called Center for Internet Security to secure our election systems.

SUMMARY: There are significant electronic voting system security vulnerabilities. When these facts are coupled with the utter lack of transparency pertaining to their operations, it is clear that election results determined by electronic voting systems cannot be trusted.
• The security vulnerabilities of electronic voting systems is well-documented.
See “Machine Vulnerabilities” for a list of many of the known vulnerabilities. These numerous security vulnerabilities were exacerbated recently by the discovery of decryption keys being stored in plain text within Dominion Election Management System (EMS) databases in multiple states.
Such negligent practices introduce the following security risks:
- Unauthorized Access and Data Breach: If decryption keys are stored in plain text, attackers who gain access to the EMS servers can easily decrypt sensitive data, such as voter information, vote counts, and election configurations. This could lead to data breaches, exposing personal information of voters and potentially compromising the secrecy of their votes[1][4][7].
- Manipulation of Election Data: With access to decryption keys, malicious actors could manipulate election data, including voter registrations, vote tallies, and election results. Such manipulation could alter the outcome of elections or undermine confidence in the electoral process[1][5][6].
- Denial of Service (DoS) Attacks: Attackers could use the decryption keys to decrypt and corrupt critical election data, rendering the EMS servers inoperable. This could disrupt the voting process, delay the reporting of election results, and require significant effort to restore system integrity[2][5].
- Spread of Malware: If attackers can access and decrypt sensitive data, they could also inject malware into the EMS servers. This malware could spread to connected voting machines and other parts of the election infrastructure, further compromising election security and integrity[2][5].
- Loss of Public Trust: The discovery that decryption keys are stored in plain text and that election systems are vulnerable to attack could significantly erode public trust in the electoral process. A loss of confidence in election security and outcomes could have long-term effects on democratic participation and legitimacy[1][5].
- Legal and Regulatory Non-Compliance: Storing decryption keys in plain text may violate legal and regulatory requirements for protecting sensitive data. Non-compliance could result in legal penalties, fines, and damage to the reputation of election authorities[4].
- Increased Attack Surface: By connecting EMS servers to the internet and storing decryption keys in plain text, the attack surface is significantly increased. This makes it easier for attackers to identify and exploit vulnerabilities, leading to a higher risk of successful cyber attacks[2][5].

Citations:
[2] https://www.nist.gov/itl/voting/security-recommendations
[4] https://metomic.io/resource-centre/plain-text-credentials
[6] https://www.comparitech.com/blog/information-security/cryptography-secure-electronic-voting-systems/
[7] https://www.passcamp.com/blog/dangers-of-storing-and-sharing-passwords-in-plaintext/
[8] https://electioncenter.org/electionresources/Internet%20Voting/e-voting.security.pdf
[11] https://www.verizon.com/business/resources/articles/s/protecting-against-election-cyber-attacks/
[12] https://nap.nationalacademies.org/read/25120/chapter/7
[14] https://www.cisa.gov/news-events/news/best-practices-securing-election-systems
[15] https://www.reddit.com/r/devops/comments/xcz764/is_it_a_bad_idea_to_store_secrets_in_code/
[17] https://www.linkedin.com/pulse/dangers-storing-passwords-your-computer-what-do-dan
[18] https://www.cisa.gov/cybersecurity-toolkit-and-resources-protect-elections
[20] https://www.politico.com/f/?id=00000172-9406-dd0c-ab73-fe6e10070001
SUMMARY: Foreign entities appear to have had significantly more access to election systems in the United States than American citizens.
• There are numerous fingerprints besides Mike’s Absolute documentary series indicating foreign interference with our elections.
See DNI John Ratcliffe “Views on Intelligence Community Election Security Analysis.” In his memo dated January 7, 2021, he states the following:
“I am adding my voice in support of the stated minority view — based on all available sources of intelligence, with definitions consistently applied, and reached independent of political considerations or undue pressure — that the People’s Republic of China sought to influence the 2020 U.S. federal elections“
The incoming DNI under the Biden Administration released a report in March that completely ignored such evidence of Chinese cyberattacks.
Investigations pertaining to the Bailey v Antrim County lawsuit revealed additional evidence of foreign election interference. Plaintiff Bill Bailey was seeking an audit of the election in the wake of a 7,060 vote flip from Trump to Biden in a traditionally Republican county. Investigations revealed evidence that the county Election Management System (EMS) server had been connected to IP addresses traceable to Tapei, Taiwan as well as servers based in Germany.

A Speckin Forensics analysis of an adjudication workstation able to modify election results in Fulton County, PA revealed that it had been connected to servers in Quebec, Canada.
Many communities throughout America contracted with SCYTL (aka Clarity Systems) to provide Election Night Reporting support services.
 The address of record for SCYTL is :
The address of record for SCYTL is :
“Scytl Secure Electronic Voting,S.A.
C/Enric Cranados 84
08008 Barcelona, Spain
Gregg Philipps and Catherine Engelbrecht of True the Vote revealed evidence that voting system manufacturer Konnech was sharing sensitive election information with the Chinese government.
We could go on, but it certainly appears that more foreign actors had access to our election systems than American citizens.
SUMMARY: Without a verifiable Cast Vote Record, we do not have an audit trail. Without an audit trail, we have no reason to have confidence in the results of a given election.
Cast Vote Records provide the election equivalent to the Scoring Summary for a football game.
It tracks who scored, how they scored and when they scored.

Despite denials by some election officials that they don’t exist, Cast Vote Records are indeed very real.
In fact, without them, it is impossible to provide an audit trail for the election results.
** Due to a protective order, the Lindell Offense Fund has removed all references to support this claim that was posted on X.com by @SheriffLeaf. **

Ballots are scanned by tabulators producing a ballot image.
The ballot image is analyzed to determine how the votes on the ballot were cast. The vote tally progression must be consistent with the ballot scanning log to have confidence that no one is manipulating the vote tally directly. All of this information is tracked in the Cast Vote Record.
During the November 2022 election, there is evidence of controlled manipulation of the sequencing of cast votes in Maricopa County, AZ.
In the documentary Absolute Proof, Mike Lindell revealed news of his possession of evidence that election results were modified as a result of foreign-based cyberattacks.
The source of this evidence is a cybersecurity expert and computer programmer by the name of Dennis Montgomery. Mr. Montgomery has developed and licensed various technologies to the U.S. government intelligence agencies including Department of Defense (DOD), SOCOM, Homeland Security (HS), Department of Advanced Naval Research (NAVY), and Air Force (AF). His detractors assert that it would be impossible for him obtain the evidence of cyberattacks upon our election system referenced in Absolute Proof. They dismiss Mr. Montgomery and the PCAPs revealing evidence of a cyberattack as a hoax. Even a cursory review of his accomplishments, however, would not lend credence to such assertions.
Dennis Montgomery is very real. During the 2022 Moment of Truth Summit in Springfield, MO, Attorney Kurt Olsen provides the definitive response to critics of him and the PCAP data he provided to Mike Lindell.
Full disclosure of the evidence possessed by Mike Lindell is currently prevented by a “state secret” protective order requested by former Director of National Intelligence, John D. Negraponte. This protective order was subsequently granted by United States District Judge Philip M. Pro.
Mike has submitted a Motion to Intervene in the lawsuit that prevents disclosure of PCAP data. The status of this motion remains unresolved.




